In India’s rapidly evolving digital ecosystem, Aadhaar remains the cornerstone of trusted identity verification — enabling millions of transactions across government, finance, telecom, and e-governance every day.
But as the use of Aadhaar expands, so does the responsibility to protect it. Rising cyber threats, unauthorized data access, and privacy concerns have made compliance with the Unique Identification Authority of India (UIDAI) more critical than ever.
To strengthen data security and governance, UIDAI released Circular No. 8 of 2025, which updates and enforces the guidelines on Aadhaar Data Vault (ADV), Hardware Security Modules (HSMs), and Aadhaar Authentication Applications. These rules redefine how regulated entities — including AUAs, KUAs, ASAs, and Sub-AUAs — store, process, and secure Aadhaar data.
.jpg)
Understanding UIDAI’s 2025 Guidelines
UIDAI’s latest mandates focus on three key pillars — secure data storage, cryptographic protection, and certified hosting environments. These new compliance norms are designed to enhance privacy, ensure operational continuity, and build citizen trust.
1. Mandatory Aadhaar Data Vault (ADV)
All entities storing Aadhaar numbers, UID tokens, or eKYC data must use a secure, UIDAI-compliant Aadhaar Data Vault. Storing raw Aadhaar numbers in open databases is prohibited. Tokenization replaces Aadhaar numbers with encrypted reference IDs, minimizing exposure risk.
2. Secure Hosting Requirements
ADVs and Aadhaar applications must be hosted only on:
- On-premises data centers (DC/DR),
- MeitY-empanelled Government Community Cloud (GCC), or
- UIDAI-approved ADV-as-a-Service platforms.
Cloud-based setups must also undergo annual SOC 2 Type II audits to verify compliance.
3. Hardware Security Modules (HSMs)
Every cryptographic process — including encryption key generation, management, and storage — must occur within a FIPS 140-2 Level 3 certified HSM. Logical partitioning is mandatory to ensure encryption keys are isolated and inaccessible to other entities.
4. Authentication Application Hosting
Applications handling Aadhaar authentication or KYC data must be hosted only on MeitY-certified cloud environments. Hosting on unapproved public clouds like AWS, Azure, or GCP is no longer permitted unless certified by MeitY.
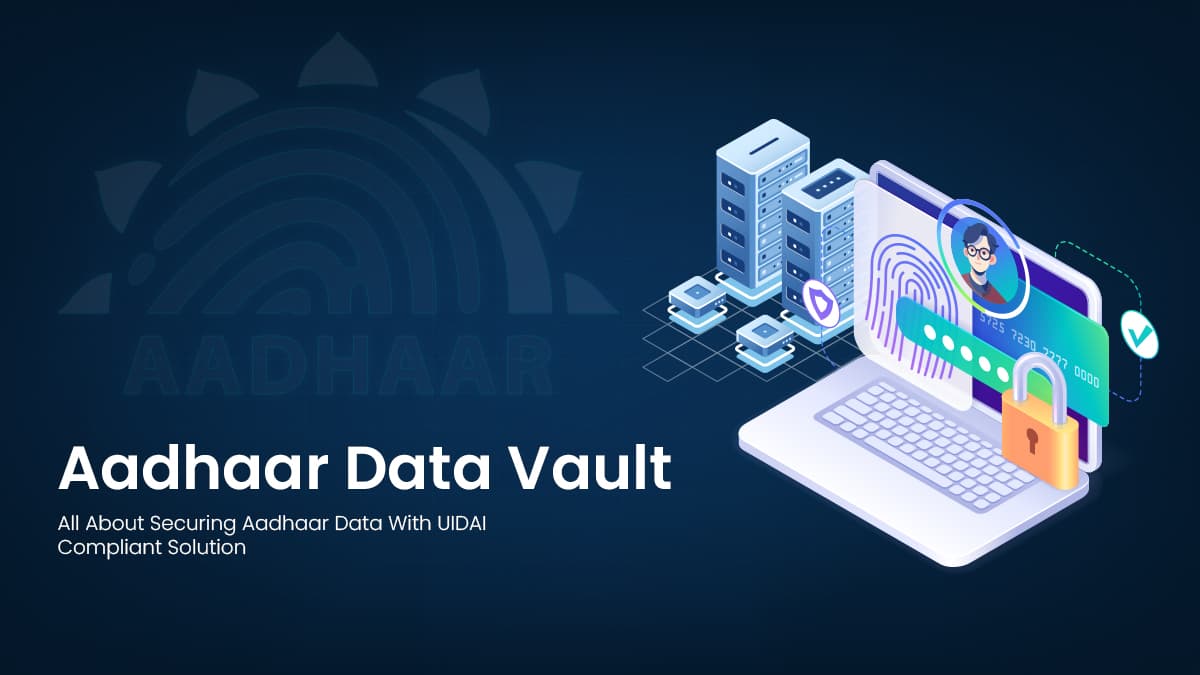
The Role of the Aadhaar Data Vault
The Aadhaar Data Vault serves as a secure, UIDAI-compliant repository for storing Aadhaar data. It encrypts and tokenizes Aadhaar numbers, provides role-based access, and maintains detailed audit trails for compliance verification.
Core Functions of the ADV:
- Encryption: AES-256 and RSA-2048 encryption ensure strong data protection.
- Tokenization: Replaces Aadhaar numbers with unique reference tokens.
- Audit Logging: Captures every access, authentication, and transaction.
- Controlled Access: Provides secure API-based integration with authentication applications.
By isolating Aadhaar data from other systems, the ADV significantly reduces the attack surface and ensures complete regulatory compliance.

Why Compliance with UIDAI’s New Rules Is Non-Negotiable
Non-compliance with UIDAI’s 2025 circular isn’t just a legal risk — it’s an operational threat that can directly impact service delivery and reputation.
1. Operational Continuity
Failure to implement compliant ADVs, host applications on MeitY-certified clouds, or use approved HSMs can halt critical identity verification processes, disrupting customer onboarding and digital service delivery. UIDAI may even revoke AUA/Sub-AUA licenses of non-compliant entities.
2. Regulatory Penalties
Violating UIDAI’s privacy and security mandates can attract financial penalties, increased scrutiny, and reputational damage under the Aadhaar Act.
3. Security Vulnerabilities
Weak encryption and improper access controls create entry points for cyberattacks, risking exposure of sensitive citizen data.
4. Cost and Complexity
Rectifying non-compliance later is more expensive — requiring major infrastructure upgrades, audits, and retraining efforts.
Compliance, therefore, isn’t optional — it’s the foundation for secure, uninterrupted, and trustworthy operations.
How REs Can Stay Ahead of the Curve
Compliance is not a future concern — it’s an immediate necessity. Here’s how regulated entities (REs) can act now to ensure adherence and strengthen their security posture:
1. Audit Your Current Infrastructure
Assess where your Aadhaar Data Vaults, HSMs, and authentication apps are hosted. Identify encryption, audit, or hosting gaps and prioritize corrective measures.
2. Adopt ADV-as-a-Service
Partner with a trusted provider offering UIDAI-compliant ADV-as-a-Service to quickly deploy secure vaults without the complexity of in-house setup.
3. Migrate to MeitY-Certified Cloud
Ensure your Aadhaar-related applications are hosted only on MeitY-approved environments to maintain licensing and operational continuity.
4. Implement Aadhaar Fraud Management Module
Set up fraud detection and prevention modules as mandated by UIDAI to proactively identify anomalies in authentication requests.
5. Strengthen Security & Monitoring
Deploy High Availability (HA) and Disaster Recovery (DR) setups, enforce robust IAM controls, and perform SOC 2 audits for continuous monitoring.
6. Train & Document
Educate teams about UIDAI compliance practices, update security policies, and maintain audit-ready documentation.
By acting proactively, REs can turn compliance into a competitive advantage — building resilience, regulatory trust, and customer confidence.
CSM Technologies’ UIDAI-Compliant Aadhaar Data Vault Solution
CSM Technologies offers a fully compliant and scalable Aadhaar Data Vault that meets all UIDAI 2025 mandates:
- End-to-End Encryption: AES-256 + RSA-2048 encryption via HSMs.
- Tokenization Engine: Converts Aadhaar numbers to secure reference tokens.
- MeitY-Compliant Hosting: Available on-prem, on GCC, or as ADV-as-a-Service.
- Integrated Monitoring: Real-time audit logs and SIEM-based monitoring.
- API-Driven Integration: Secure communication with Aadhaar-based applications.
With successful implementations such as Odisha Aadhaar Authentication Framework (OAAF) and Bihar Aadhaar Authentication Framework (BAAF), CSM has processed over 1.86 billion authentications — proving that strong security and scalability can coexist seamlessly.
Turning Compliance into Opportunity
Beyond regulatory alignment, UIDAI compliance offers strategic benefits:
- Builds public trust through transparent and secure governance.
- Ensures operational continuity even under audit scrutiny.
- Reduces risk of fraud, downtime, and cyber incidents.
- Enhances brand credibility in the digital identity ecosystem.
Conclusion
UIDAI’s 2025 guidelines mark a pivotal shift in Aadhaar data security — transforming compliance from a checkbox to a strategic advantage.
By adopting secure Aadhaar Data Vaults, deploying certified HSMs, and migrating to MeitY-compliant infrastructure, organizations can safeguard citizen data while ensuring uninterrupted, trustworthy service delivery.
As India continues its digital transformation journey, compliance with UIDAI’s mandates isn’t just about data protection — it’s about protecting trust, transparency, and the future of digital governance.








































We will verify and publish your comment soon.