Imagine trying to navigate the modern world without proof that you exist. No bank -account. No SIM card. No vote. No healthcare. For roughly 1.1 billion people globally- the “invisible billion”, this isn’t a thought experiment. It’s a lived reality. A billion living in oblivion!
In the digital age, identity is no longer just a document. It is a doorway to healthcare, education, welfare, banking, voting, and dignity itself. Yet for over a billion people worldwide, that doorway remains firmly shut. Designing digital identity systems that leave no citizen behind is therefore not merely a technical exercise. It is a societal choice, one that reveals who a nation sees, who it serves, and who it is willing to forget.
Digital identity has quietly become the spine of modern governance. When it works, public services flow seamlessly, fraud shrinks, and citizens move through life with fewer frictions. When it fails, people vanish into administrative shadows, unable to claim benefits, prove existence, or exercise rights. Inclusion, then, is not an aspiration. It is the design brief.
 (1).jpg)
Beyond Metrics: Inclusion as Empathetic Design
At the global level, SDG 16.9 mandates universal legal identity by 2030, quietly powering at least ten interconnected development goals, from poverty’s banishment and gender equity to safer, more dignified migration pathways. But inclusion cannot be reduced to dashboards and progress trackers. It is not a numbers game. It is empathetic cartography.
It demands mapping invisible barriers, discriminatory civil registries that quietly sideline girls, biometric blind spots that fail persons with disabilities, and procedural rigidities that treat human lives as edge cases. Recent forums such as the 2025 India–West Asia Dialogue surfaced a hard-earned truth. Adoption follows alchemy, not authority. Utility and trust act as catalysts. Mandates function like poisons.
People do not embrace digital identity because they are compelled to. They adopt it when it feels instinctive, respectful, and useful. A good system behaves like a familiar hearth - warm, reliable, and woven into daily life, not a distant edifice guarded by protocols and passwords.
Scale, Universality, and the Aadhaar Paradox
India’s Aadhaar, a 1.3-billion-strong behemoth, illustrates both the promise and peril of scale. It has channelled nearly $1.7 trillion in welfare transfers (Source: World Bank estimates), sharply reducing leakage and friction. Yet it also walks a razor’s edge on privacy, reminding us that magnitude amplifies consequences. When identity becomes infrastructure, every design choice, what data is collected, who can access it, and how redress works, shapes citizenship itself.
This is why universal coverage must be the starting point but never the endpoint. Legal identity should extend from birth to death, without discrimination based on gender, ethnicity, disability, income, or geography. But universality that ignores context is fragile. Systems must recognize that identities are not static. Names change. Biometric markers fade. Cultural notions of identity differ. Designing for edge cases is not charity. It is systems thinking.
 (1).jpg)
Law, Privacy, and Implementation as Inclusion Tests
Equally foundational are robust legal and regulatory frameworks. Technology without law is power without restraint. Inclusive digital identity systems require clear legislation governing data collection, usage, sharing, and retention, crafted through public consultation, enforced by independent oversight, and backed by accessible grievance redress mechanisms. Without this, trust erodes, and adoption stalls.
Privacy by design is not a slogan. It is an architectural principle. The most resilient systems practice data minimalism, collecting only what is necessary and revealing only what is relevant. Verifying age without exposing a birthdate. Confirming eligibility without exposing identity. When systems respect user agency, they replace surveillance anxiety with quiet confidence.
Implementation is where inclusion is either honoured or betrayed. Digital-only approaches are exclusionary by default. True inclusion demands omnichannel access, mobile apps and web portals, but also physical enrollment centers, assisted registration, offline verification, SMS-based services, and community outreach. Digital divides are not just about connectivity. They are about literacy, language, disability, and trust.
 (1).jpg)
How CSM is engineering Trust at Scale Through Digital Identity
At CSM Technologies, we approach digital identity not as a standalone technology layer, but as critical public infrastructure that underpins trust, inclusion, and efficient governance. Our digital identity management solutions are purpose-built for GovTech environments where scale, security, and compliance are non-negotiable. From Aadhaar-linked authentication to end-to-end identity lifecycle management, we help governments design systems that are secure by design, compliant by default, and intuitive for citizens to use.
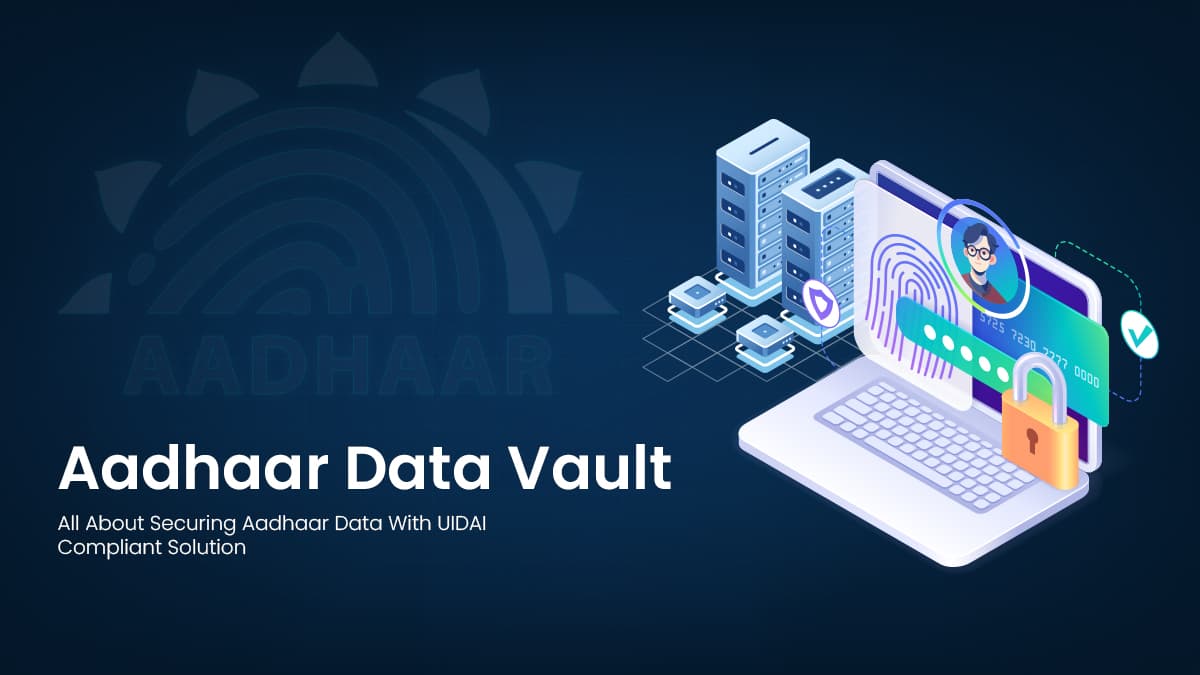
Our capabilities span Aadhaar Data Vaults compliant with UIDAI guidelines, browser-based eSign platforms, and enterprise-grade identity lifecycle frameworks that manage identities from creation to retirement. By integrating strong encryption, blockchain-based tamper resistance, and workflow automation, our solutions ensure sensitive identity data remains protected while enabling frictionless digital service delivery across sectors such as land management, education, mining, and social welfare.
A defining example is the Odisha Aadhaar Authentication Framework (OAAF) co-developed with the Odisha IT Department. Acting as a centralized authentication gateway, OAAF enables seamless Aadhaar-based verification for an array of government departments, reducing duplication, improving accountability, and accelerating citizen service delivery at scale.
Beyond platforms, our Digital Identity Management System knowledge assets and real-world deployments, including Krushak Odisha and SPDP demonstrate how identity-led architectures can translate policy intent into measurable impact. In essence, CSM builds future-ready digital identity ecosystems that strengthen governance, enhance citizen trust, and make inclusion operational, not aspirational.
 (1).jpg)
Trust, Interoperability, and the Future of Identity
Interoperability and open standards complete the picture. Digital identity should act like connective tissue, securely linking health, finance, education, and social protection systems without locking governments into proprietary silos. Open, modular platforms prevent vendor lock-in, reduce costs, and future-proof national infrastructure.
Yet no system succeeds on architecture alone. Trust is the real currency of digital identity. It is earned through transparency, local-language awareness campaigns, citizen participation, and the humility to course-correct. When people are treated as co-creators rather than data points, adoption becomes organic.
Looking ahead, the future of digital identity may paradoxically involve less identity, not more. Systems that verify attributes without revealing individuals, architectures that prioritize dignity over data hoarding, and governance models that assume accountability as a given. The question is no longer whether digital identity will shape governance, but whether it will do so humanely.
A world where identity is not a privilege but a public good, secure, voluntary, privacy-preserving, and universally accessible. When digital identity systems are designed with foresight and compassion, they do more than authenticate individuals. They acknowledge existence, enable dignity, and make citizenship real.
The invisible billion are waiting. The question is whether we will build bridges or walls.







































We will verify and publish your comment soon.